🛡️Trustline Disclosure Guide
Welcome to Trustline Disclosure guide for organization. This guide will help you to launch and manage your Vulnerability Disclosure Program (VDP) by providing you with step-by-step instructions.
Overview
Trustline Disclosure revolutionizes the approach to vulnerability management by providing organizations with a structured framework for receiving and addressing vulnerability reports from ethical hackers and security researchers. This program ensures transparency, security, and prompt resolution of vulnerabilities, thereby enhancing overall cybersecurity posture.
Pre-requisite
To launch your Disclosure, some prerequisites need to be in place. These include:
Subscription: Verify that your organization has subscribed to Trustline platform, specifically the package that includes the Disclosure program.
Pre-defined asset: There should at least be one defined asset which can be done in asset management.
Getting Started
1. Request a Disclosure Program
1.1 Access Trustline Platform
Log in to Trustline platform and navigate to the Disclosure section to begin.
1.2 Creating a New Program
To initiate a new Disclosure program:
Click on the Create Program button.
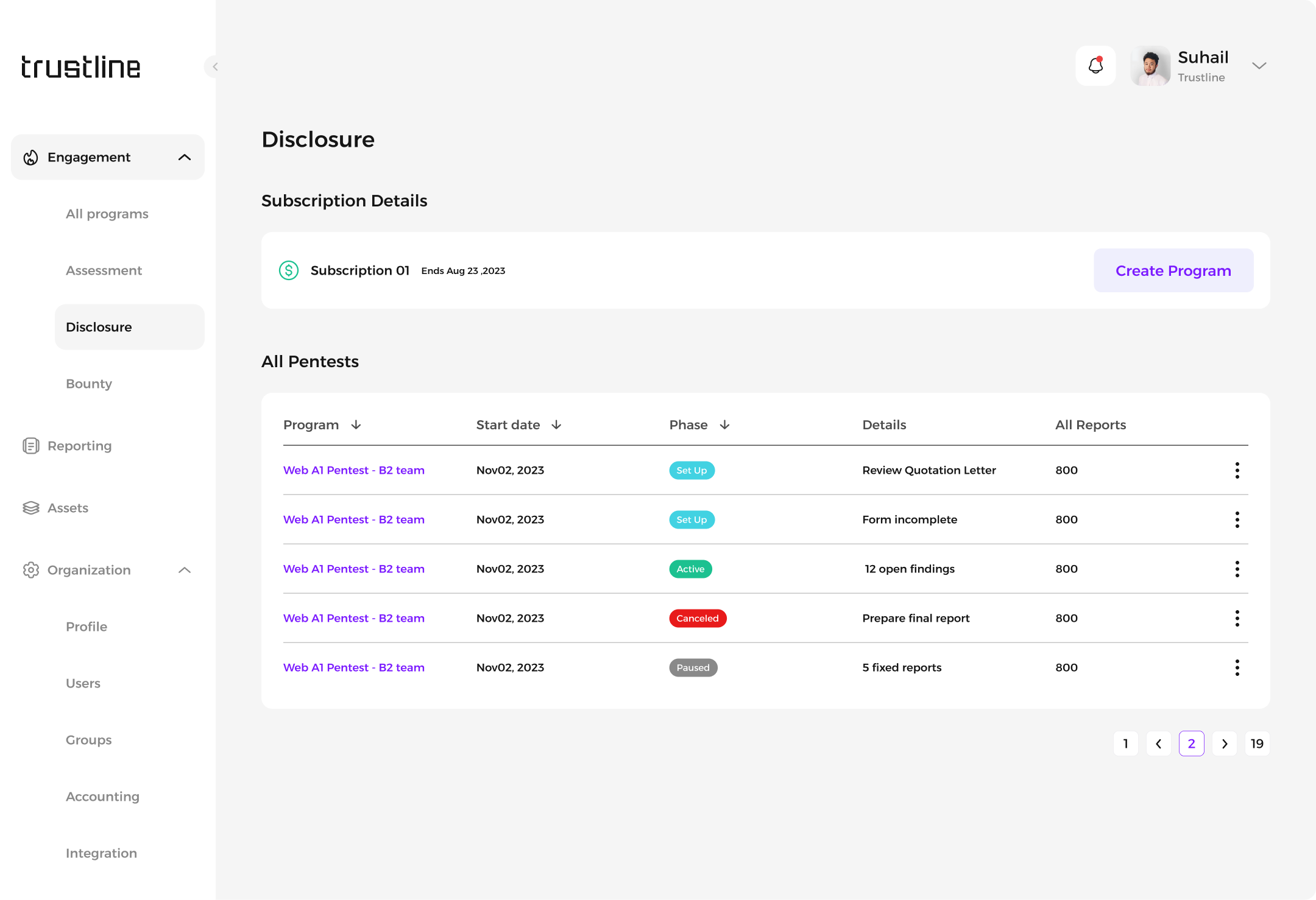
Enter the program details in the pop-up window:
Name
Start date
Website
Assets to be tested
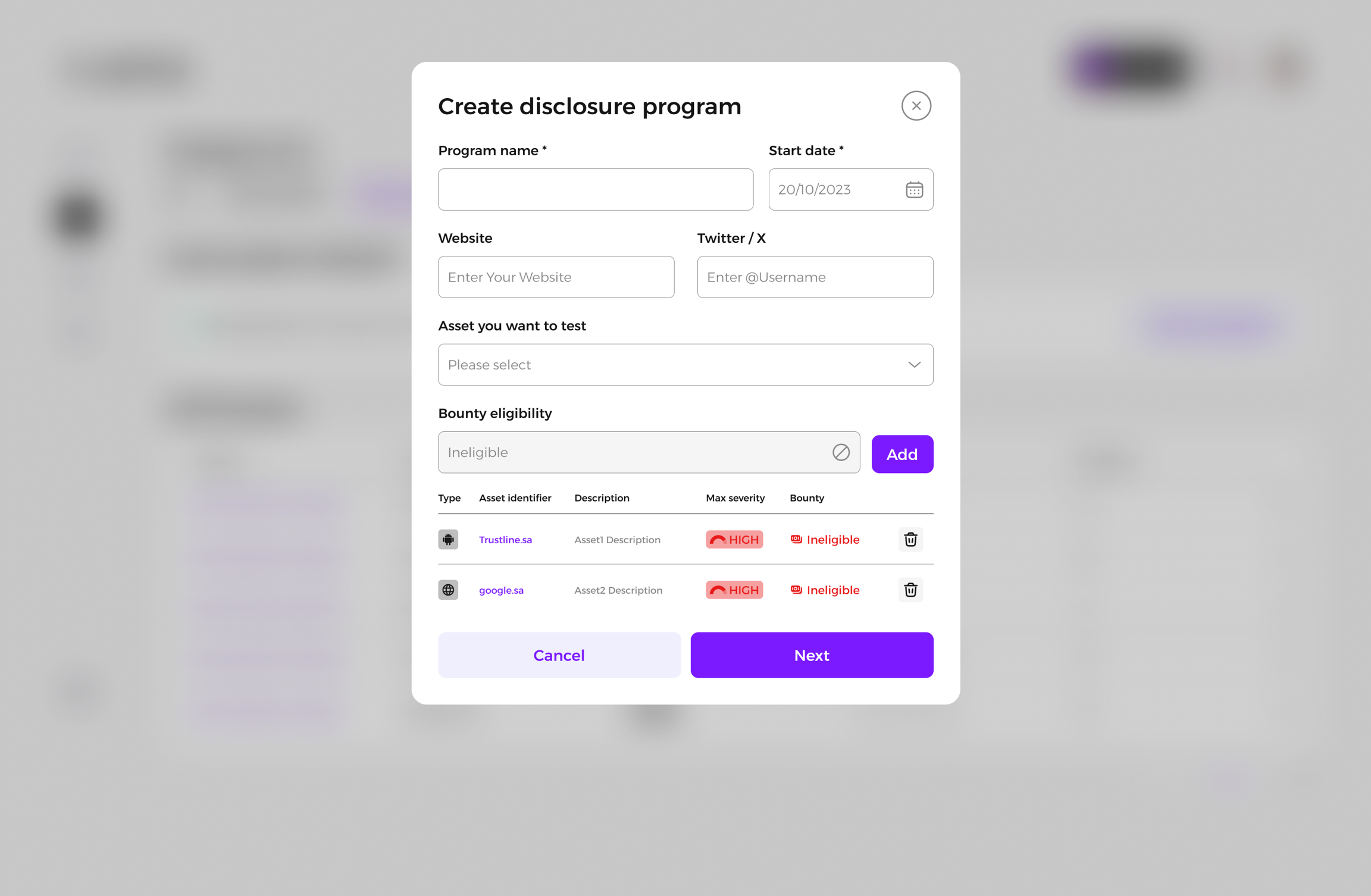
Attach any necessary files.
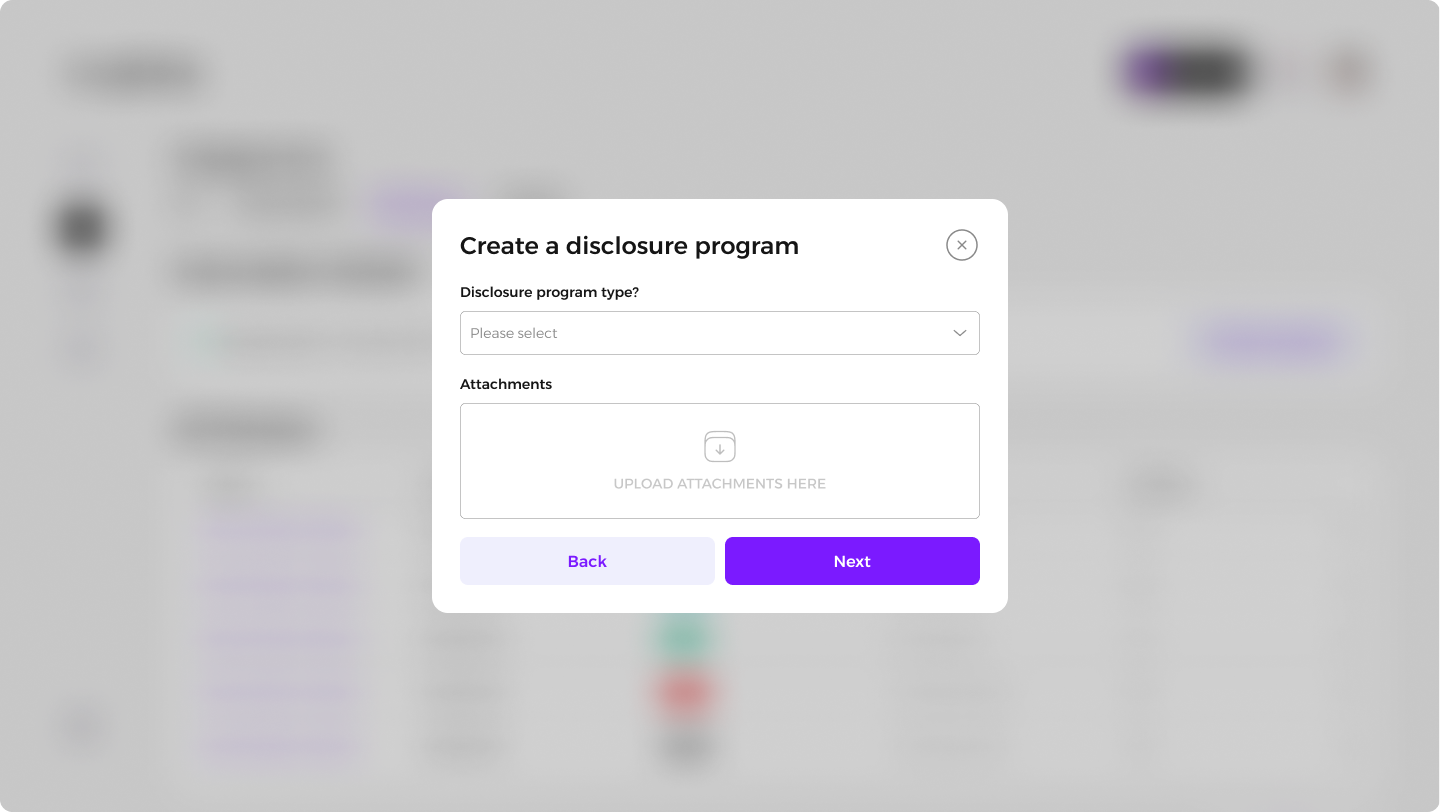
Enter the policy details outlining the program's guidelines.
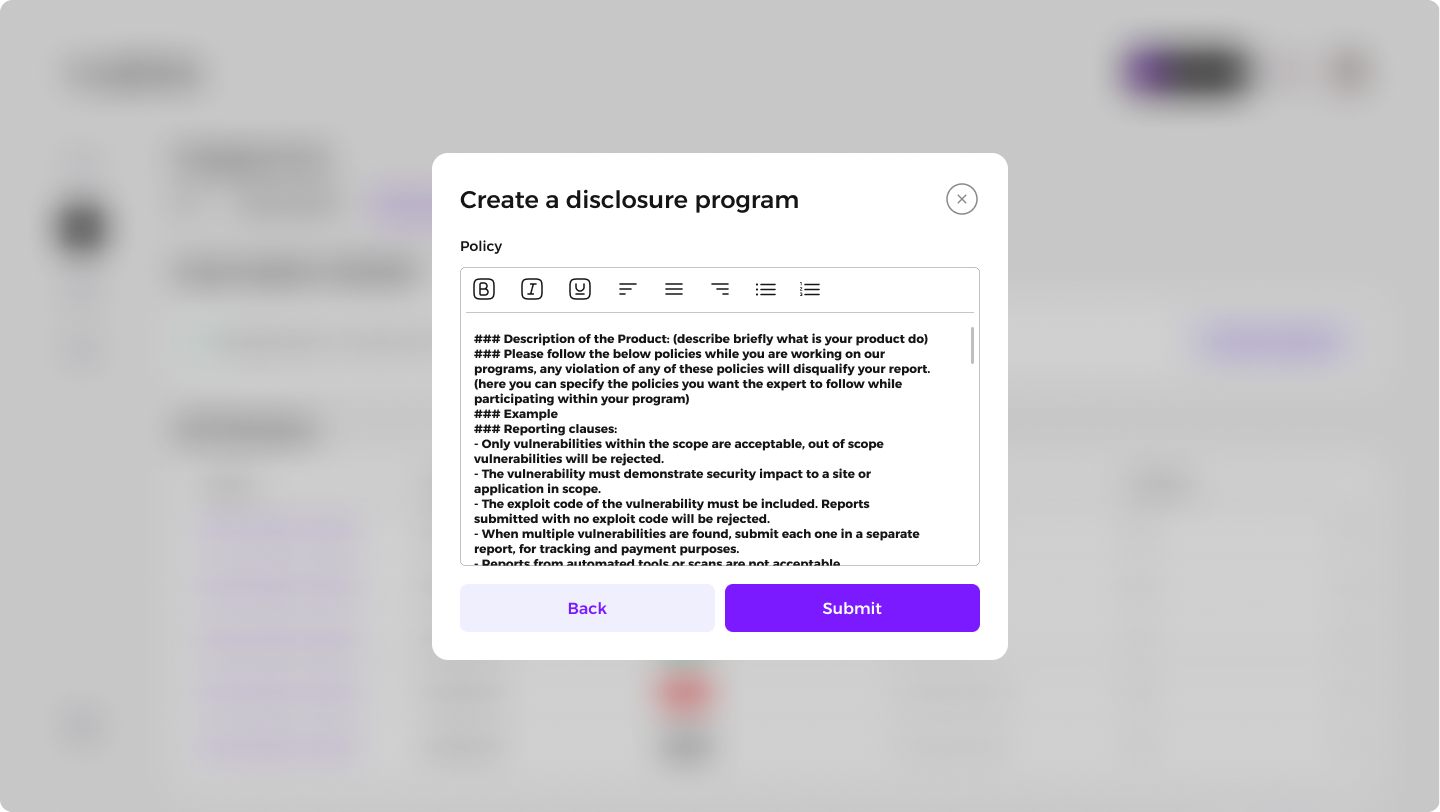
Click Submit to create the program and receive a confirmation notification.
Trustline will activate the program after it is created and once all necessary evaluations are complete.
2. View and Manage the Disclosure List
2.1 Program Details
To access comprehensive details of a Disclosure program:
Navigate to the engagement page on Trustline.
Click on the program name in the table to view:
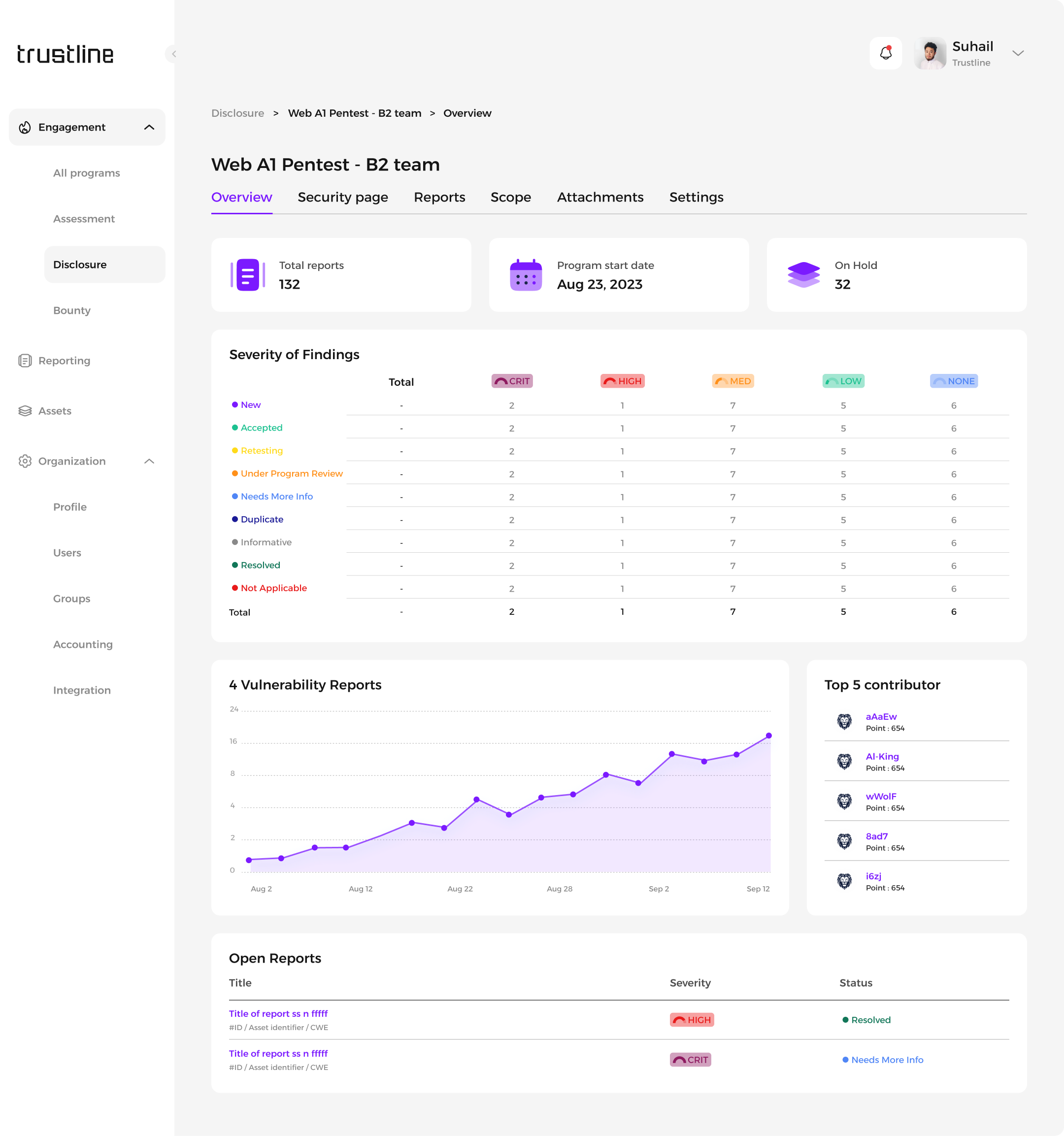
Overview: Total number of reports received, Program start date, Number of assets within the program's scope, severity of findings, vulnerability reports, Top contributors, and Open reports.
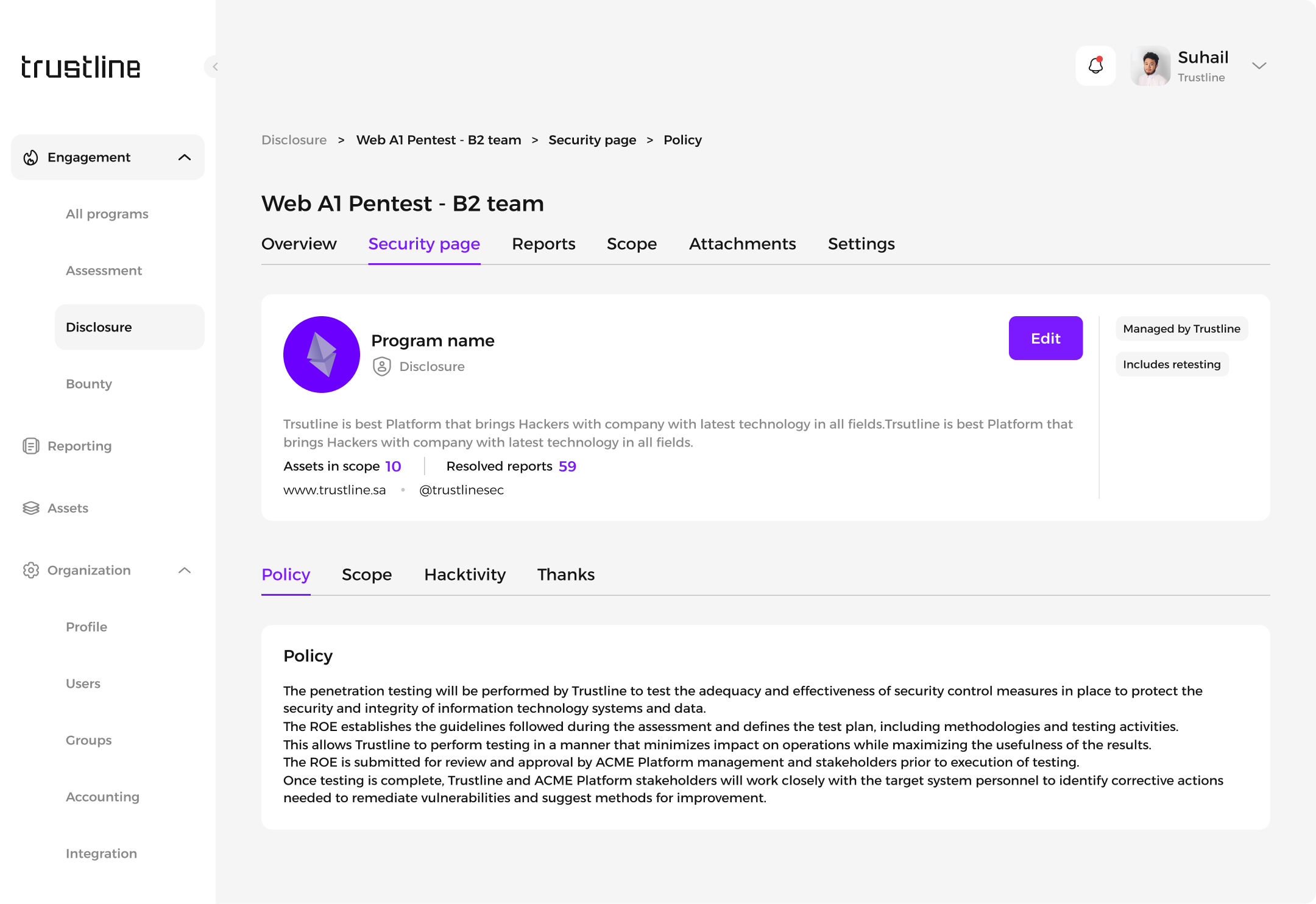
Security page: Displays various sections including policy, scope, Hacktivity, and Thanks.
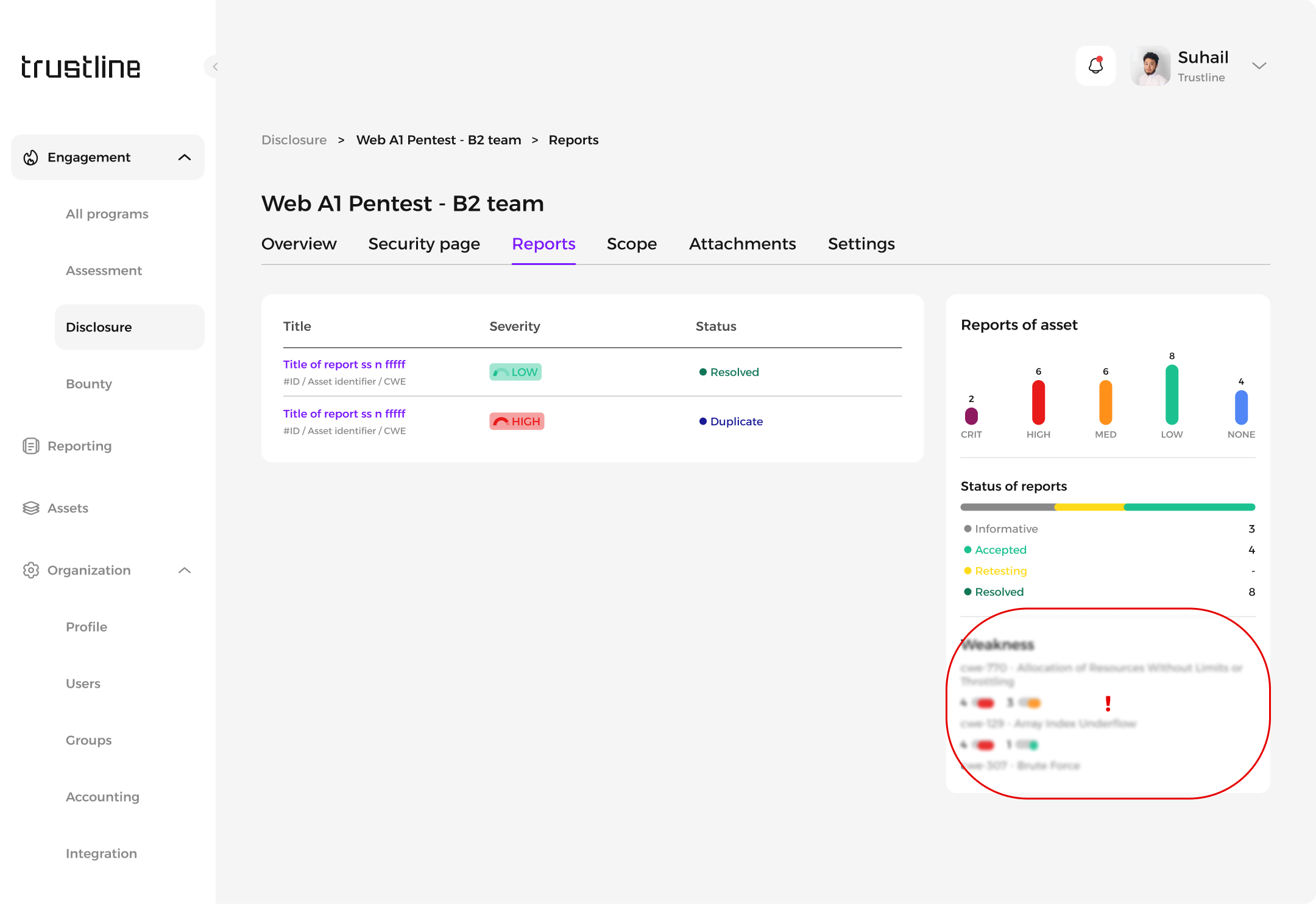
Reports: Submitted vulnerability reports with severity and current status.
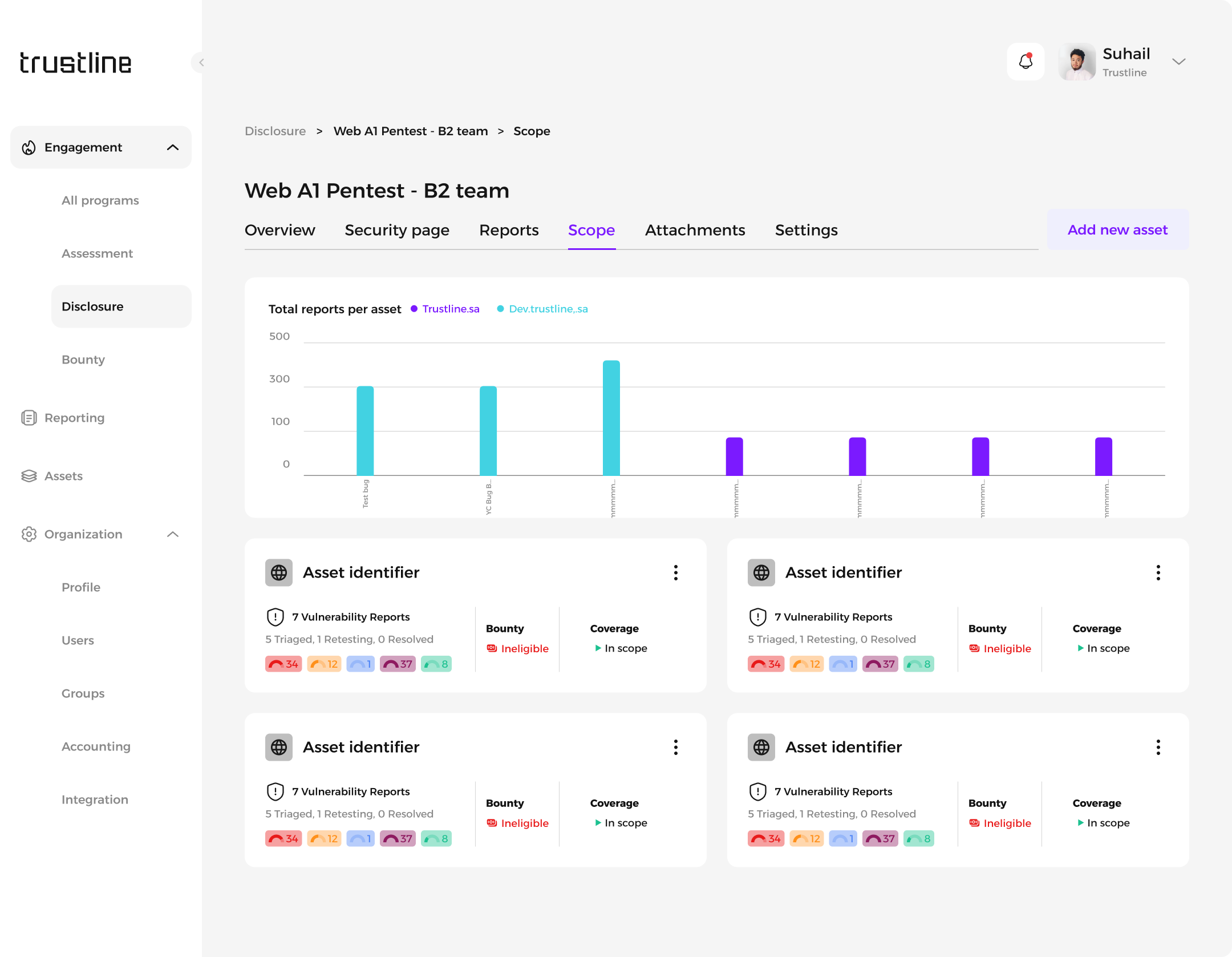
Scope: Details of assessed assets, including types, identifiers, and status.
Attachment: Management and display of assessment-related files with an option to remove attachments if needed.
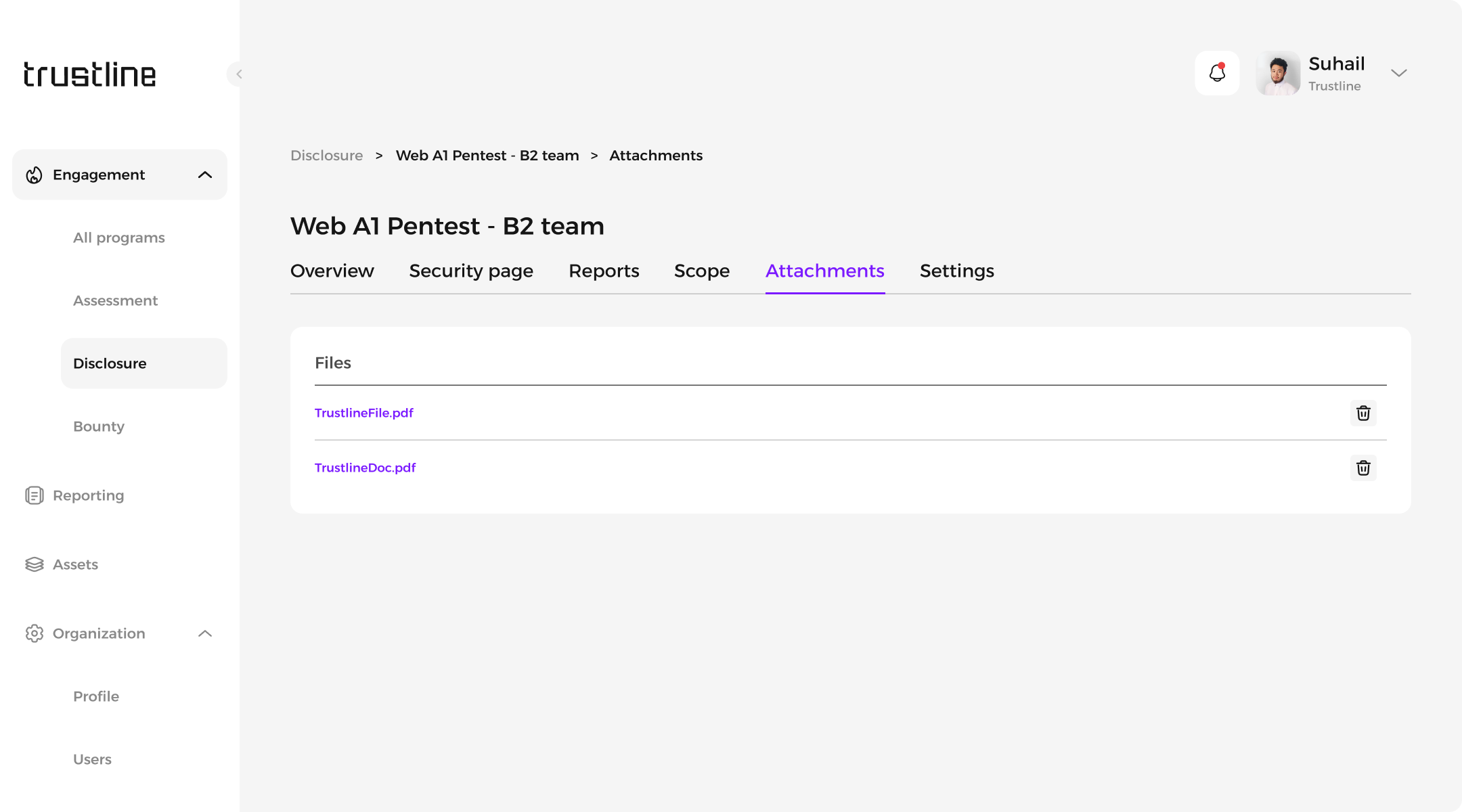
Settings: Configuration of program preferences and settings.
3. Managing Disclosure Program Settings
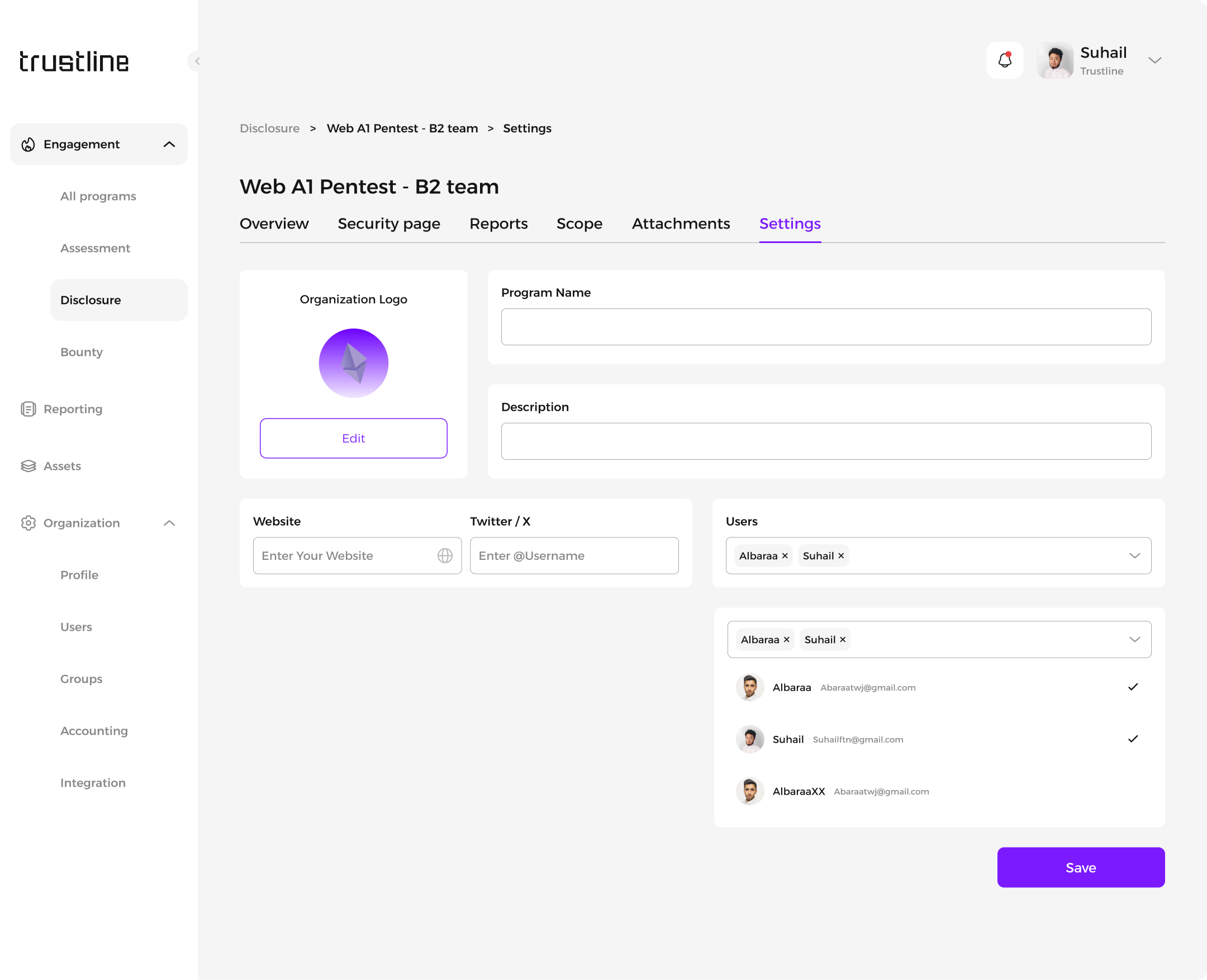
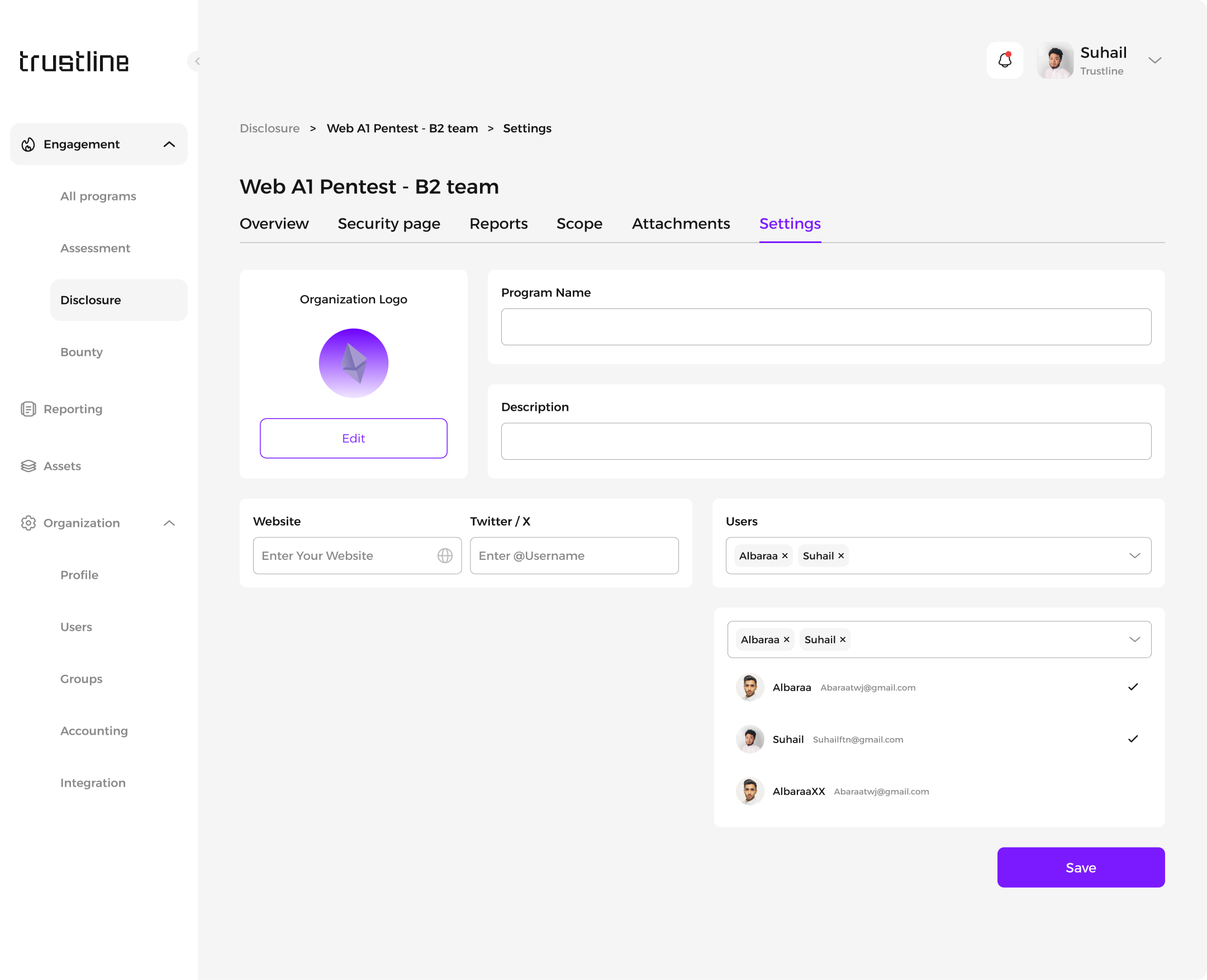
3.1 Program Settings
To adjust program settings and details:
Navigate to the settings section of the specific Disclosure program.
Modify program details such as:
Program picture
Name
Description
Website
Associated Users: Manage user access and permissions as needed.
4. Update Disclosure Program
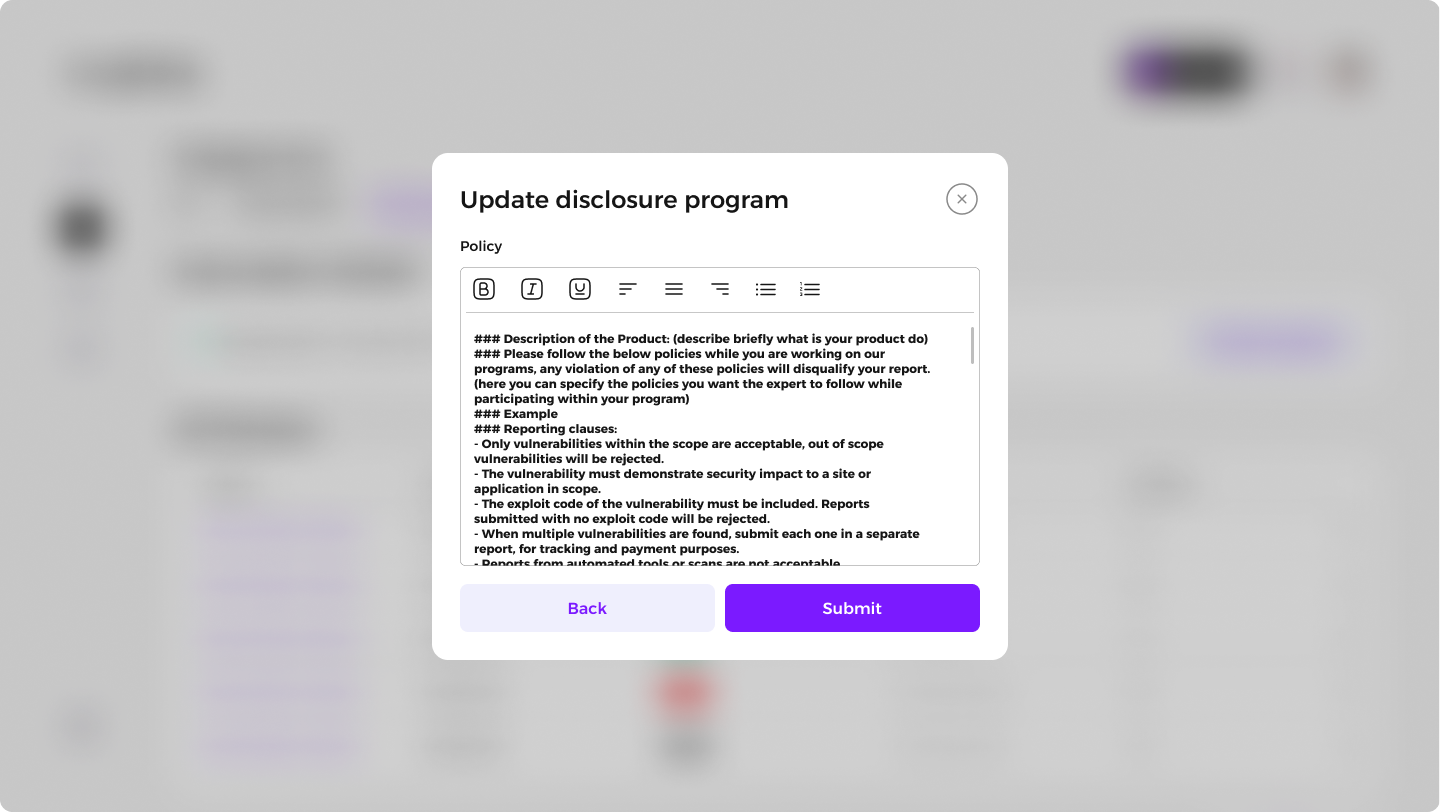
4.1 Updating the Policy
To modify the Disclosure program's policy:
Navigate to the Security Page of the specific program.
Click the Edit button next to the program details.
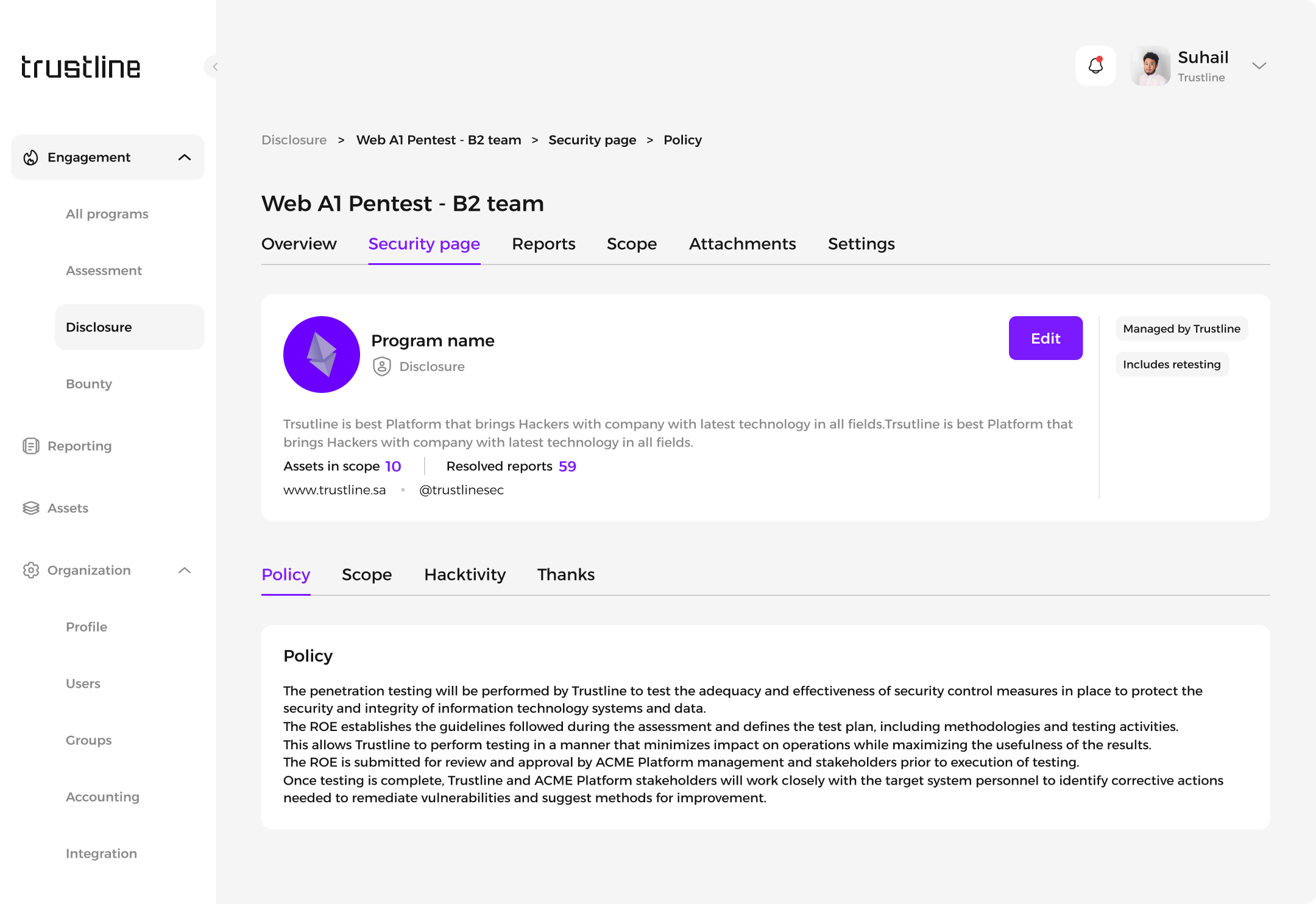
Update the policy details as necessary and save the changes.
4.2 Updating the Scope Assets
Navigate to the Scope section of the specific program.
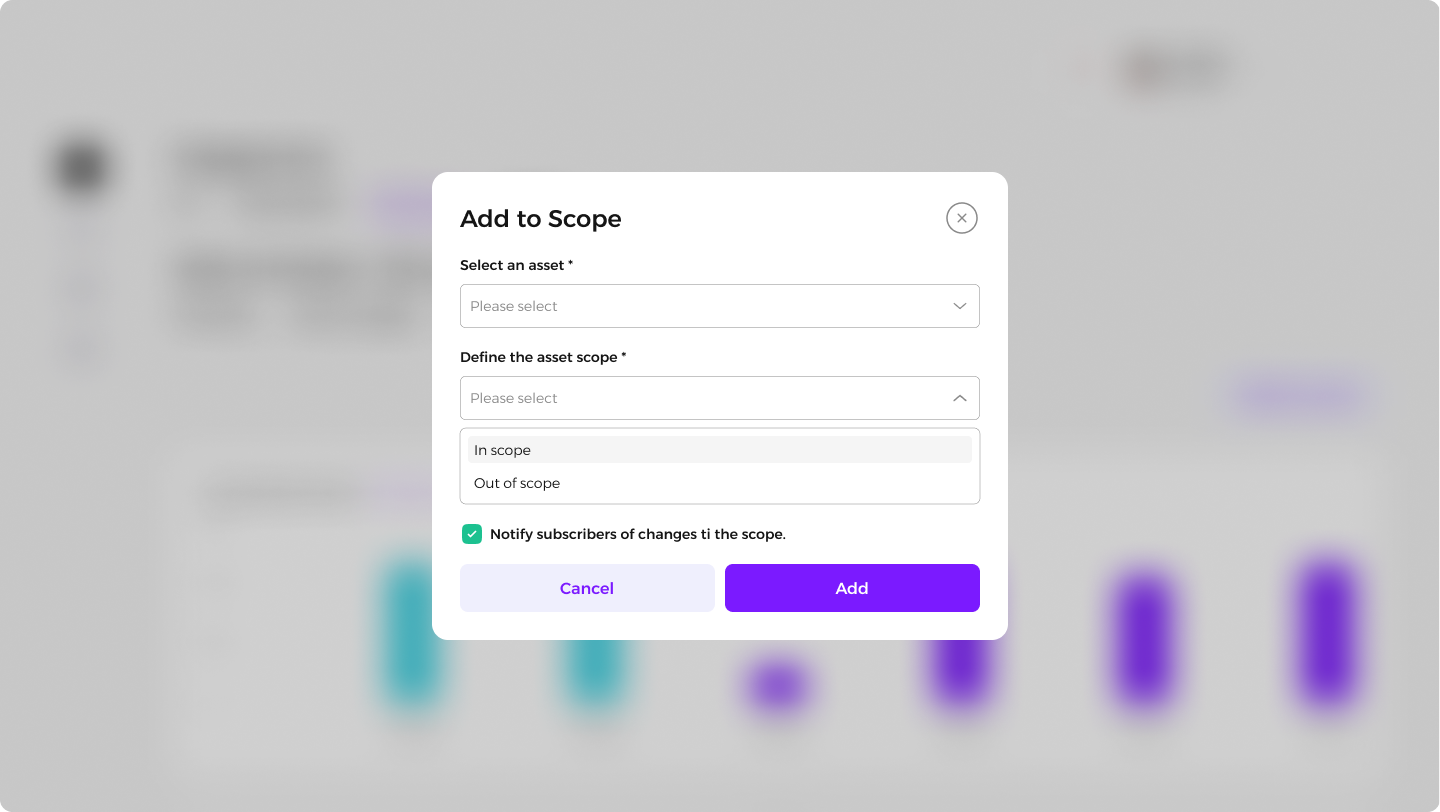
Adding New Assets:
Click Add New Asset.
Select the asset type and define its scope.
Editing Assets:
Use the dropdown menu for a specific asset.
Select Edit Asset to modify its scope and notification preferences.
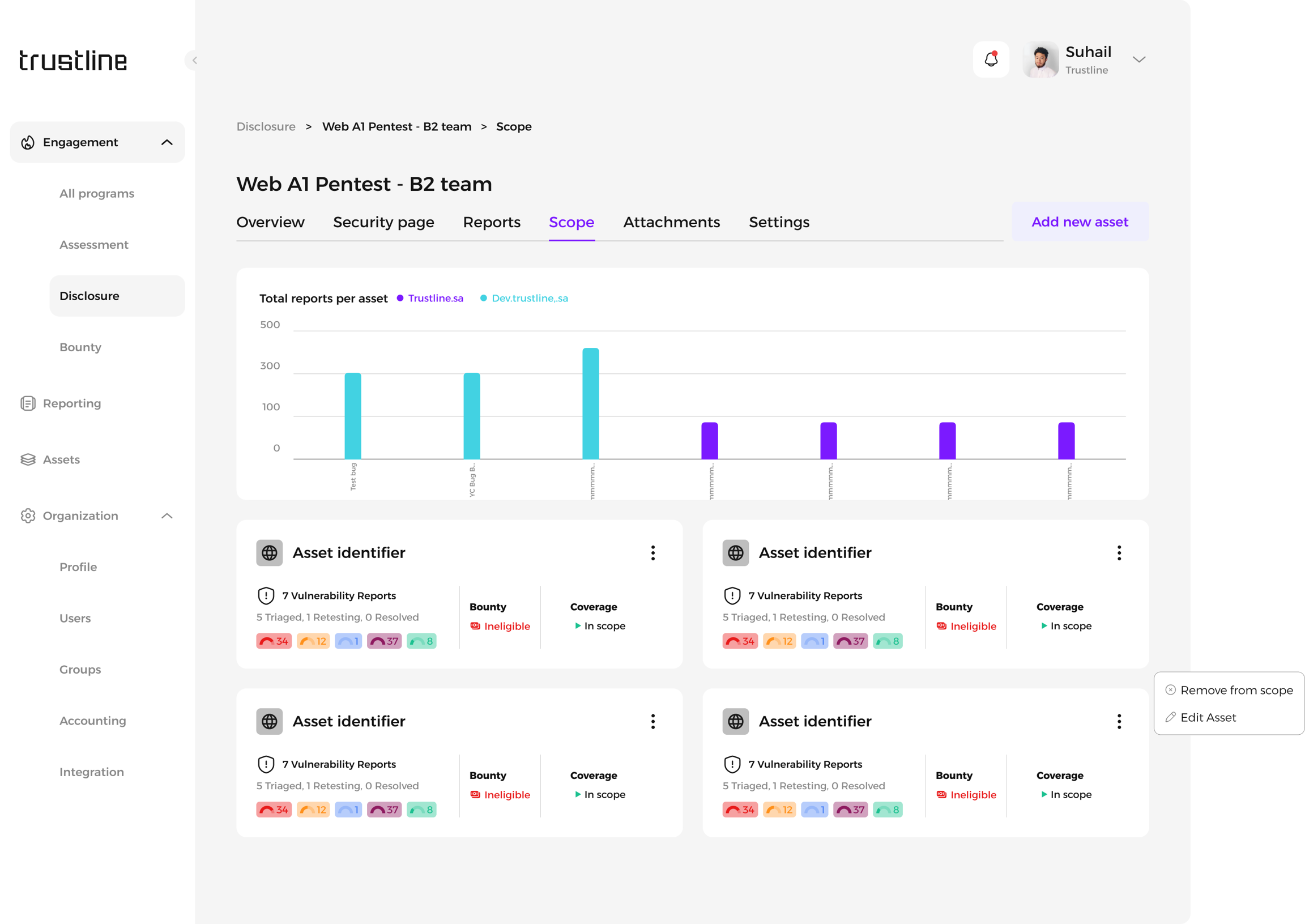
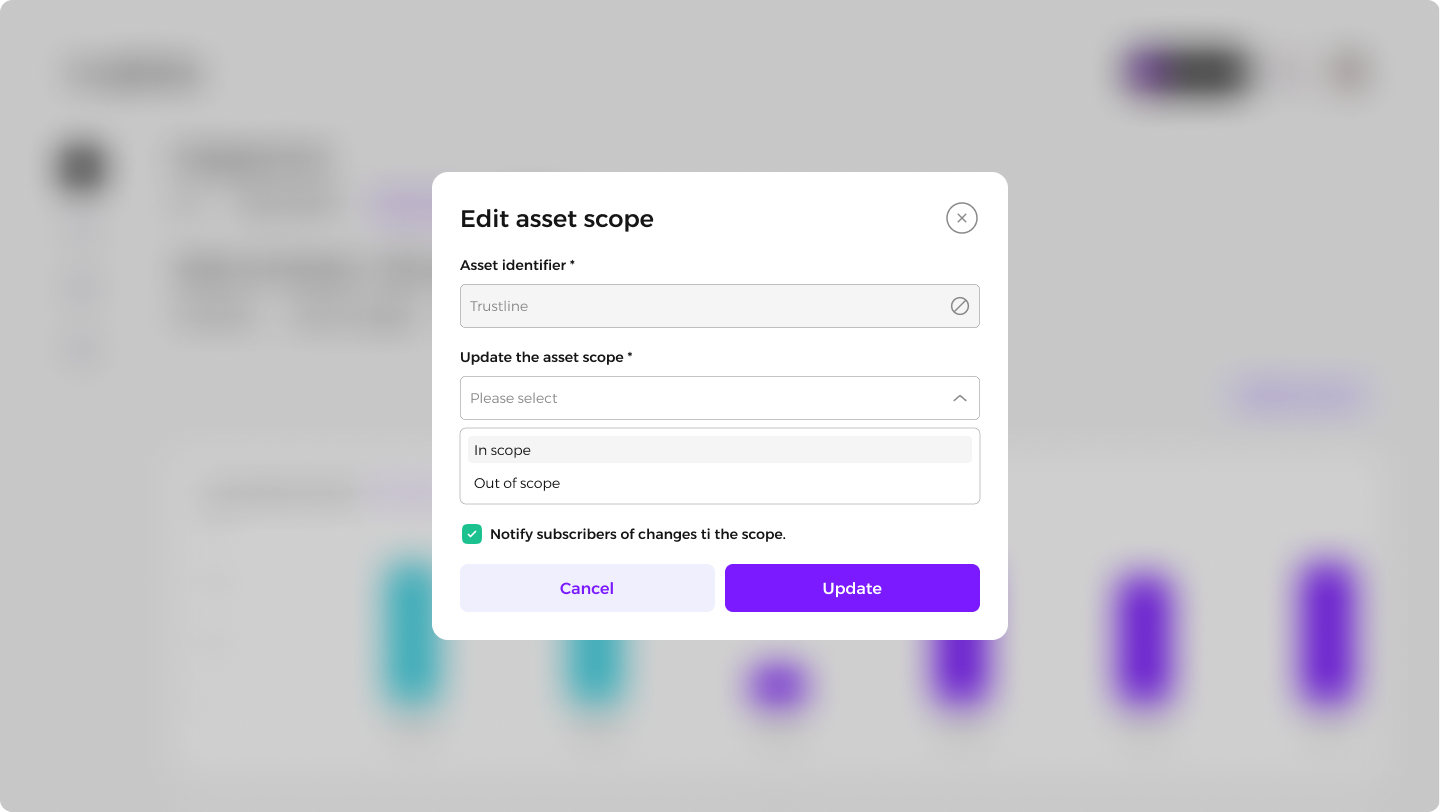
Removing Assets:
Use the dropdown menu for a specific asset.
Select Remove from Scope to exclude it from the program.

5. Real-time Findings
Prompt reporting of vulnerabilities through our platform ensures continuous disclosure updates. Hackers are encouraged to report findings immediately. Check here for details onManage Reports Guide
6. Request Retesting
During this stage, you can request a retest for any finding you have fixed to validate the fix.
Check here for details on Retesting Guide
7. Managing the Program Status
7.1 Controlling the Program Status
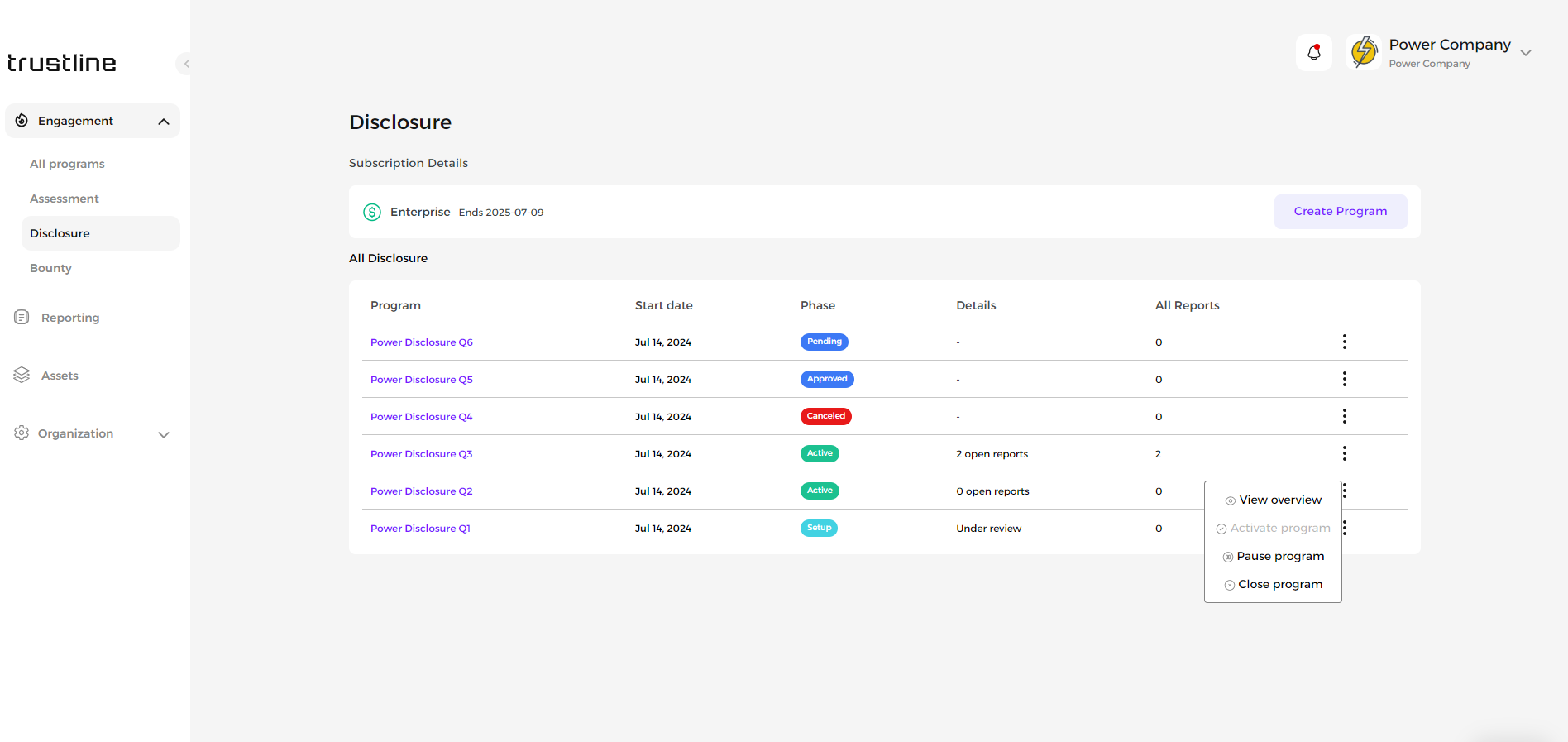
To manage the status of a Disclosure program:
Access the list of active Disclosure programs. then, from the dropdown menu, select one of the following options:
Activate Program: The program is live and hackers can submit vulnerability reports.
Pause Program: Temporarily suspend acceptance of new reports.
Close Program: The program is closed permanently.
References
📄Manage Reports Guide🔄Retesting GuideLast updated
