📄Assessment Testing
Overview
1. Real-time Communication

2. Real-time Findings
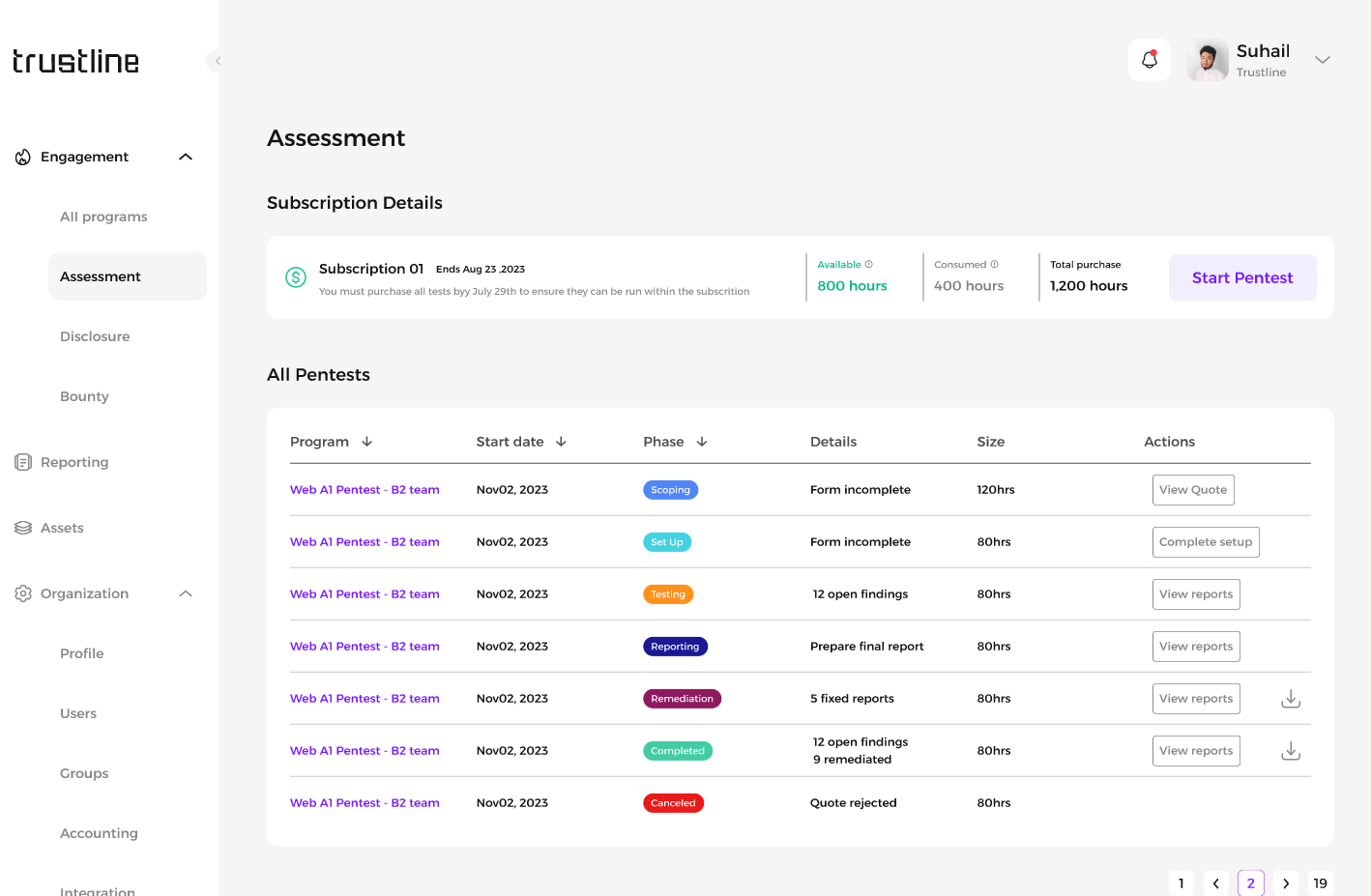


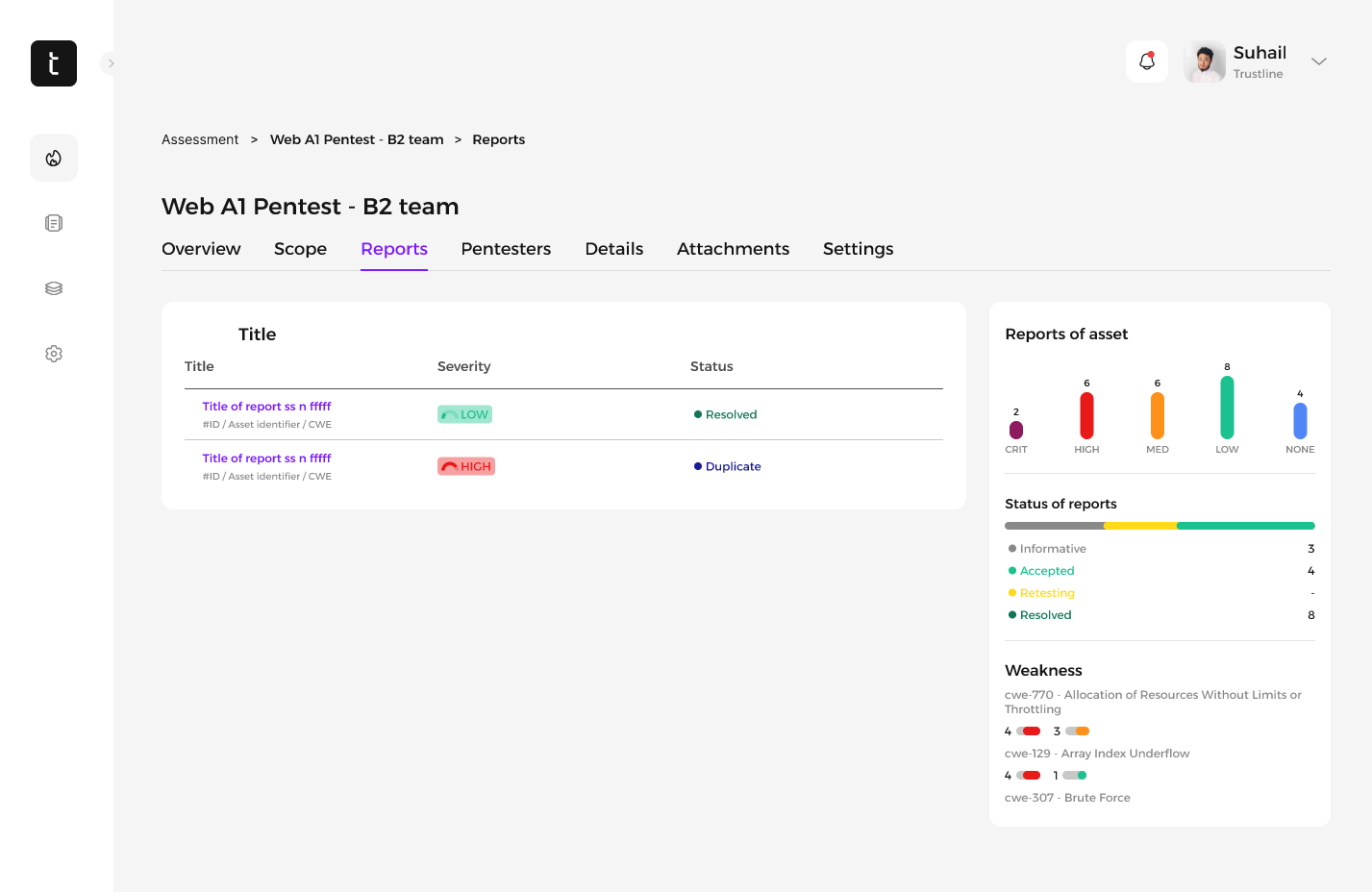



3. Updating Assessment Phase to Reporting
Related Articles
🔎Assessment Scoping⚙️Assessment Setup⬇️Assessment Reporting🔁Assessment Remediation✔️Assessment CompletionLast updated
